SOC
To me, it was quite obvious raising security within the company (mainly because of GDPR) was not so much about Policies, but more about awareness, and to some extent, tools and process. Making coworkers aware, making sure they stay aware and, in some cases the most difficult part, making them accept some minor adjustments such as the need for an anti-malware client on their precious computer - that was the real challenge! Ok, so I had made sure the company had policies, and I had been part of making sure the company was prepared for GDPR. But I knew the work so far would be worth nothing unless we had an entity in the organization maintaining and protecting it!
The vision
Around Christmas time (late 2017), the CDC project had entered into implementation mode. Me and the Swedish branch IT-crew had gathered together with our partner (around 6 consultants) at our CoLo (DigiPlex) in the northern suburbs of Stockholm. We pulled up at the parking lot (after having passed through the guarded gate, surrounded by barbed wire fences) in 4-5 different cars, CIA style. With us we had brought all the new shiny hardware that was to be mounted and cabled. After a couple of hours of standing in our CoLo cell with our hands in our pockets, trying not to be in the way of the consultants flurrying about, racking and cabling and putting labels on stuff, me and the Swedish IT crew decided to retreat to the facility’s flagship conference room. I decided this was a perfect time to launch my plan regarding InfoSec.

Armed with a marker and a white board, I drew up my thoughts, trying to get the guys engaged. I emphasized the need for a SOC that was not just about monitoring, maintenance and incident response, but also awareness and PR. I drew an orgchart where the SOC needed close ties to HR and local management teams. I elaborated on possible scenarios and challenges, and how I envisioned the day-to-day tasks. Questions where handled, hurdles where addressed and I got thorough to them. That was the first step. I had buy-in from the most important people; the IT guys.
Organization
Of course my Boss was already aware of my plans to form a SOC, hell she was the one assigning me with raising security in the company! But I knew security was not on the agenda elsewhere in the company, so next step was to get buy-in from all management regarding my plans to form a SOC. I threw some slides together, ran them buy my boss and then presented them to the Nordic Management Team a couple of weeks later.
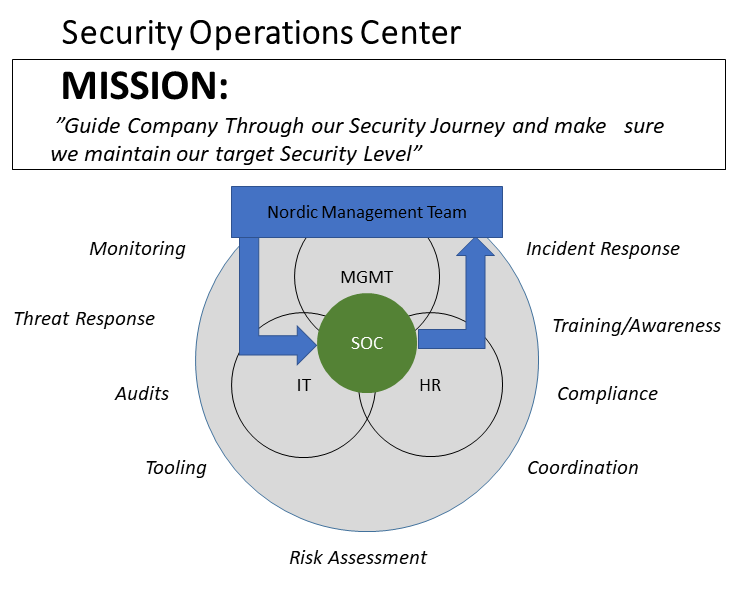
In the defining image of what Company SOC really is supposed to be, I decided to put SOC somewhere in between Local HR, IT and Local Management. IT of course needs to be there, but in my vision HR and Management is equally important. I imagined all our fancy tools and processes sooner or later would lead to us facing an incident. And that incident would involve one ore more employees, therefore the need to get HR on board. The subject of the incident might not like the fact that we (the SOC) tells him/her what to do, especially if it involves some sort of restriction on their digital freedom. To avoid feelings getting hurt, I decided management (local and top level) needed to be sign off on the SOC mission. They needed to a approve what we should monitor, and at which incidents we should intervene. I decided to assign Fredrik with the role of “Head of SOC”, also naming our external consultants and the collaboration framework we would use in the SOC. Also be vary clear about the chain of command, since when shit hits the fan, we won’t have the luxury of being all touchy-feely consensus about the actions taken. The NMT approved. The company SOC was born.
Tooling
As described in Security Governance, we had decided to focus on these threats:
- Compliance (GDPR)
- Theft
- Disruption
We selected and implemented tools that we saw fit for defending us from these threats, with focus on interfering as little as possible with the company processes and way of working. Email security was of course a priority. We selected Centium on top of the already existing security features of Office 365. Also, being a digital agency and using a myriad of different tools and systems, most of them being SaaS based, more or less without restriction, a modern CASB solutions was needed in our arsenal. Since we had prior experience with Netskope and was very satisfied so far, that choice was easy. Perimeter protection was considered, and since we had prior experience with Forty, the choice fell on FortiGate. We decided to also sign up for Forty Indicator of Compromise, an add-on feature to the Forti Analyzer central log management system. We have not yet gained very much from IoC, it seems to be a quite immature product so far. Or, we just don’t get compromised… The hot potato was end-point protection. I kind of didn’t want that at all, having had nothing but bad experiences with the likes of Avast, FSecure, Panda, Symantec, Trend Micro et al. In my experience, none of them worked properly, especially on Mac (we’re 70% mac), and it was source of constant user frustration and admin headache. But the consultants insisted we needed antimalware agents on everyone’s computers, so I reluctantly accepted. They recommended Carbon Black Defense (together with Carbon Black incident response), and I had no objection. The system (CbDefence) is very capable, and their “next gen” pattern recognition features are powerful. But just as I thought, the management overhead is big and user frustration level sometimes high. This is not necessarily because of Carbon Black, but more an effect of the very fabric of our company culture and environment. The roll-out is still on-going, to be honest, it’s a fucking pain in the ass. And, even though the rest of the SOC disagrees, I’m still not convinced it’s worth the effort. Besides pure InfoSec tools, we did a big job securing our central applications and systems, such as Slack, Dropbox, Office 365 etc, utilizing their built-in features for monitoring and access control.
Process
The SOC set about trimming our tools and discussing scenarios. There’s a good plan for what to do in what scenario. But we’ll come across scenarios we have not prepared for sooner or later, and it will be interesting to see how we cope with those. And there’s stuff we don’t agree on. For example, should we care about Porn and bitTorrent? Both, one could argue, are sources of malware. One of them is (almost exclusively) used for illegal activities (piracy), and the other one may breach Company Code of Conduct but is (usually) legal. Everyone in the SOC, including my boss and the consultants, think we should block BitTorrent and Porn on company equipment and network. The SOC could of course easily monitor and block it on the network and/or the devices. But there’s no fucking way I’ll do that without explicit go-ahead from the whole management team! Why, you may ask yourself? Well, the company prides itself on being very loose with policy, and letting all employees make decisions for themselves. For example, we let employees chose their computers (almost) without restriction. Everyone is admin on their machine. The company encourages employees to use their company equipment for private stuff as well. The company is very scared to restrict creativity! And, believe it or not, I think this is a good thing! Let employees do their job with “freedom under responsibility”, I say. The only control needed in a consultancy-based organization is result (billability) and customer satisfaction! Let the teams solve their problems in whatever way they see fit! I’m sure that will create a better product, and it sure as hell makes recruitment easier when show-casing the very free environment we possess! It just nurtures a higher level of commitment when failures can only be blamed on oneself! The SOC just have to adopt to this and make the best we can out of this culture, is my stance. So what about BitTorrent and Porn? Well we brought it to the top-level management team to let them decide whether to block it. They decided not to. I’m glad they did! The company has kept its soul. At least for the time being.
Conclusion
Collaboration, tooling and (most) incident response procedures are working well so far. Involvement from HR, not so much. They basically fail to see their part in the security part of the organization. It’s high on my to-do to make them understand. Awareness is difficult. We made a presentation and toured the offices to explain the policies and give practical examples on how to act in different situations, what we monitor and what to expect from the SOC. But it’s difficult to get through. There’s fifty-fifty between suspicion of something bad (personal restriction and/or more work) and just not giving a crap. I thought GDPR would have helped us get enough attention to get through to the employees. But sadly, there’s still lot of work to be done here, in order to PR. But at least we have buy-in from the account managers! They have to face a plethora of security related questions when bidding for customer contracts! And all of a sudden, they have a document ready to be attached to the offer (the company Security Governance)! This really sets us apart from other digital agencies. We have come a long way in regard to InfoSec, and the others, well they have nothing. But me becoming the acting legal department, reading DPAs and contracts and answering endless customer questions, well that’s not always super fun, and honestly, should be done by the customer facing people themselves. But I know that’s part of building trust for SOC. And trust is the only way to realize my vision to its full extent. So I try to educate and self-empower them while I do their job… I also envisioned me not being actively involved in the SOC by now. You know, just saying yes or no to some strategy decisions and being available as a source of authority during incidents. But we’re clearly not there yet, and I’ll need to plan for some more rolling up of sleeves. Especially on the PR and awareness parts of the SOC.
The personal experiences, viewpoints and opinions expressed in this blog post are my own and in no way represent those of the company.
